TorBox v.0.5.0 is a major upgrade because starting with this version, it not only can be used to help clients to access the Internet safely and circumvent censorship, it also allows to bring your content in a safe and uncensored way to the Internet. Again, nyxnor, with his OnionJuggler project, was a key driver behind the Onion Services implementation into TorBox. With this version, TorBox introduces Onion Service support to share a simple website or/and files through Onion Services. However, this is only the start; in subsequent versions, we plan to support Onion Service access management on TorBox itself, and also a secure chat module is already programmed by Zotil but not yet implemented due to a lack of time. The support of Onion Services has much potential for developing TorBox further, but because our time is limited, it is essential that you give us feedback, what you need and want to see in the next version. Please feel free to use the discussion forum to tell us your needs.
TorBox Image (about 985 MB): v.0.5.0 (02.01.2022) – SHA-256 values
TorBox Menu only: v.0.5.0 (02.01.2022) – SHA-256 values
Since we had to install additional software packages and update the configuration files, it is necessary to use the new image or to reinstall TorBox using one of our installation scripts.
Besides the support of Onion Services, TorBox brings additional updates, improvements and fixes:
- Update: The system is based on Raspberry Pi OS “Bullseye” lite with Linux Kernel 5.10.63 and Tor version 0.4.6.9. This version fixes several bugs from earlier versions of Tor. One important fix is the removal of DNS timeout metric from the overload general signal. During our test, we had the feeling that Tor version 0.4.6.9 works more stable and reliable than the versions before. All installation scripts are updated to work with Raspberry Pi OS “Bullseye”, Debian 11 and Ubuntu Server 20.04.3 LTS / 21.10. Additionally, we also updated TorBox’s internal list of OBFS4 bridges.
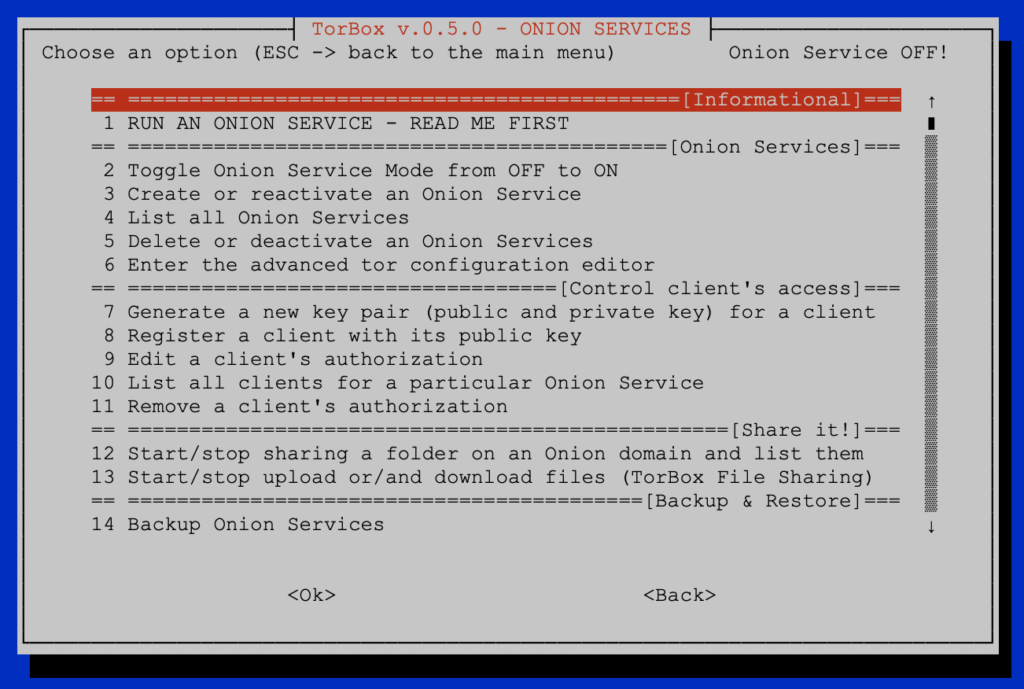
- New: The introduction of an Onion Services implementation allows the creation of Onion Services for public use or only for selected clients using client access restrictions. With the Onion Services sub-menu (found in the “defend the open Internet” sub-menu), it is easy to share a folder with a static webpage, files etc. on an .onion domain with our without client access control, even if the TorBox is located behind a firewall, a network translator or placed in a censoring country. With TorBox File Sharing (TFS), upload and/or download files can be allowed to the public or specific clients.
- New: Since 2021, the TorBox team observed more and more providers (especially in connection with open hotspots) blocking ports needed for tor to work properly (tor commonly uses ports 80, 443, 9001 and 9030 for network traffic and directory information). Therefore, TorBox uses by default countermeasures against a tightly configured firewall taking care that tor uses only ports 80 and 443 for its data stream. We didn’t observe any negative impact (nevertheless, probably this feature should be deactivated if a bridge relay is run on the TorBox).
- New: torrc is now edited by nyxnor’s vitor, which checks the accuracy of tor configuration inside torrc before saving the new configuration file. This should avoid a broken tor configuration by using the advanced tor configuration editor. Vitor is part of the OnionJuggler project. Also, after changing tor’s configuration, TorBox is asking to restart tor.
- New: The team has been working hard to improve the code’s quality and introduced some basic coding guidelines, which we will implement step by step in the coming up versions. Also, we started to check the code with ShellCheck. Thanks to nyxnor for the inspiration!
- Improved: The “first-use” script introduced in TorBox’s last version had some major shortcomings, expecting the Internet is connected to the Ethernet interface. With TorBox v0.5.0, the “first-use” script was extensively rewritten. It supports now all the usual connection types. Additionally, if the countermeasures against a tightly configured firewall setting should stay activated, what we highly recommend.
- Improved: As part of our new basic coding guidelines, we rewrote the “Update and Reset” sub-menu, now called “Update and Maintenance”. At the same time, we improved the update routines, which also updates the installed Python modules and Snowflake (if tor is updated). The ability to remove all OBFS4 Bridge Relay Data was moved into the OBFS4 Bridge Relay sub-menu.
- Improved: The TorBox Wireless Manager (TWM) is now sorting the list of available wifi along with the signal strength. Hidden networks are only displayed after pushing the H key to declutter the main screen. Also, the code under the hut was again optimized (for example, a timeout was added if the AP doesn’t respond after sending a wrong password, optimizations for small screens and more).
- Improved: If TorBox’s WLAN is permanently disabled, the TWM tries to reconnect to a Wireless Network on
wlan0, not only onwlan1. However, ifwlan0andwlan1are available, TWM will prioritizewlan1(in this case, we think there is a reason why an USB wifi adapter is connected to the TorBox ?). This also fixed an issue mentioned by connected201. - Improved: TorBox’s Automatic Counter Measures (TACA) checks after reconnecting with a wifi network if the interface got an IP address from the remote DHCP server. If this is not the case, it restarts the interface, triggering the request for a new IP. Also, TACA will detect if the system time is out of sync and re-synchronize it with ntpdate.
- Improved: Captive Portals are a pain in the ass! If the login page cannot be reached for whatever reason, TorBox provides a direct way back into the TWM (network reset included) to try it again. We have the experience that Captive Portals are getting harder to pass. However, currently, we are experimenting with another alternative way to deal with Captive Portals. If successful, we will add it immediately to TorBox v.0.5.0, which will be available after updating the TorBox menu in the “Update and Maintenance” sub-menu.
- Improved: Cable support is easier to accomplish now. We reviewed and simplified the code to achieve this goal. Consequently, we merged
set_interfaceandset_captiveintoset_interface_2andset_captive_2and removed the older files. This also fixed an issue mentioned by connected201. - Improved: Usability of the Countermeasure against a disconnection when idle feature.
- Improved: The tor log file is now shown with a filter to declutter the output, and “Bootstrapped 100% (done): Done” message is highlighted in white.
- Improved: The Bridge Relay backup file is placed into
~/backup. - Fixed: In the expert mode of the tor install scripts and the “Update and Maintenance” sub-menu, a hiccup due to a broken sort algorithm prevented the showing up of tor x.x.10 versions.
- Fixed: Even TorBox’s WLAN was permanently disabled, it was activated again when using
wlan0as an Internet source. This bug was reported by connected201. - Fixed: Snowflake is running again.
- Security: We must mask both tor services to ensure no use of tor connections before configuring TorBox with the “first use” routine.
- Security: Since the last TorBox version, all access to a tor related URL (for example,
torproject.org) directly from the TorBox have been done through tor for security reasons. Thanks to an advice from nyxnor, we switched to a more secure curl SOCKS5 method (curl -x socks5h://127.0.0.1:9050). - Removed: Display of the Vanguards log because there is nothing interesting to see.
We need your feedback!!
We hope this version pleases you. However, we are dependent on feedback. It is not just about fixing bugs and improving usability, but also about supporting additional interfaces and hardware in future releases:
- What do you like?
- What should be improved (why and how)?
- What would you like to see next? Which features do you request?
With the TorBox GitHub repository, it is straightforward for everyone to report issues or change the code and propose it in a pull request. Because we continue to travel around, it sometimes needs more time to address the issues and proposals.
For future versions, it is essential that we know what you need and want to see from the Onion Services implementation. Please feel free to use the discussion forum to tell us your needs.
Known problems and bugs
- BUG: Due to a little bug in the script, The menu entry, which should only activate OBFS4 bridges, which are ONLINE, fails to activate the OBFS4 mode properly. This bug also prevents TorBox to deactivate the OBFS4 lines in the tor configuration file. It can be fixed by updating the TorBox menu in the Update & Maintenance sub-menu (entry 5) and by choosing “Force to deactivate the OBFS4 mode” in the same sub-menu (entry 10). The image file is not fixed yet — PENDING! ⏳
