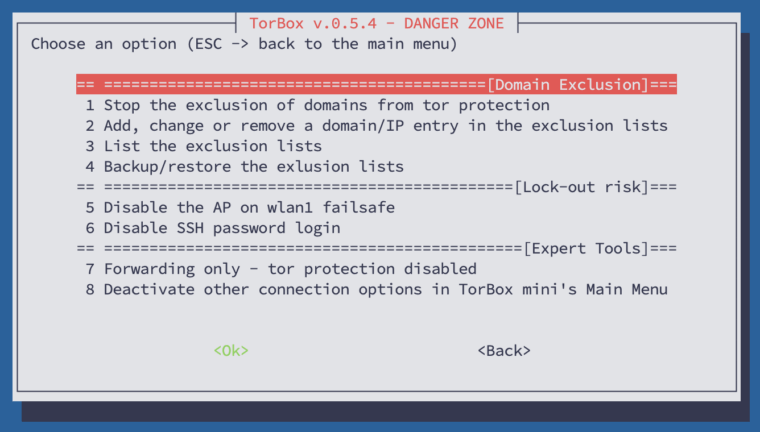
This sub-menu comprises features that are considered risky or could compromise the user’s security and anonymity. Therefore, these features should only be used if the user knows the potential risks and consequences. In the following, we look at all menu entries one by one:
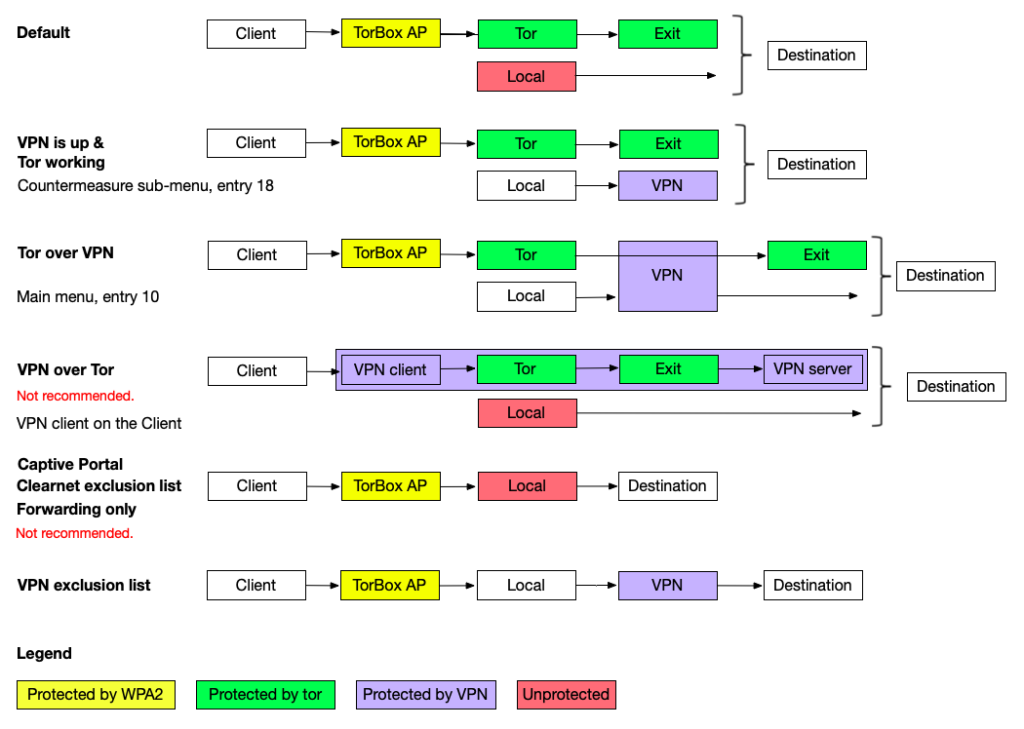
- Menu entry 1: Start / Stop the exclusion of domains from tor protection: If this feature is started, TorBox will connect certain domains directly, meaning that these domains will NOT BE ROUTED THROUGH TOR. These domains are provided by the user and can be categorised into two buckets: CLEARNET and VPN. If you put a domain into the CLEARNET bucket, TorBox will always contact this domain directly. In the VPN bucket, TorBox will only directly contact the domain if the TorBox is connected with a VPN provider (either in the main menu entry 10 is chosen or entry 18 in the Countermeasure sub-menu is activated).
This feature was a request from a user who wanted specific governmental sites in an authoritarian country to be connected directly, rather than through Tor, even though he used Tor for all other connections to protect himself. Another use case could be excluding a streaming service that doesn’t require protection (for example, a local music station) but uses a significant amount of bandwidth. Please note that Tor does not protect traffic to or from IPs on the exclusion list. It would be best to assume that everyone will see that you connect these IP addresses. If not encrypted correctly (for example, by using HTTP, which is blocked by default), everyone can view the content of the communication to and from these IP addresses.
- Menu entry 2: Add, change or remove a domain/IP entry in the exclusion lists: Let’s say you don’t want the streaming from
netflix.comto be routed through Tor. In this case, this menu entry, the domainnetflix.comcan be added to the exclusion list. Suppose the domain isn’t already in the exclusion list. In that case, you must choose which bucket the domain should be placed in: CLEARNET (always contact this domain directly) or VPN (only contact the domain directly if the TorBox is connected to a VPN provider). After this first step,netflix.com(or better, the associated IP addresses) will be excluded from Tor routing. The entry in the exclusion list looks like this:netflix.com 52.38.7.83 44.242.13.161 44.240.158.19
Next, the option for a deeper scan is offered, which makes sense in more complex situations (load-balanced sites, requests from apps, etc.) when additional subdomains or more IP addresses need to be excluded. It is essential that the domain is used as usual on the client during the deep scan, as the scan is listening to DNS requests on the client’s interface. However, this can be a bit challenging because your client browser or/and the operating system usually cache the DNS response (the IP address) for some time. Using another browser to connect or flushing the DNS cache of your browser will help. Another method is flushing the DNS cache of your system and then using ping (for example:ping netflix.com) on the client machine. How to flush the DNS cache of an operating system or a Chrome-based browser, see here. The scan automatically stops when it has enough data and shows you the screen below:
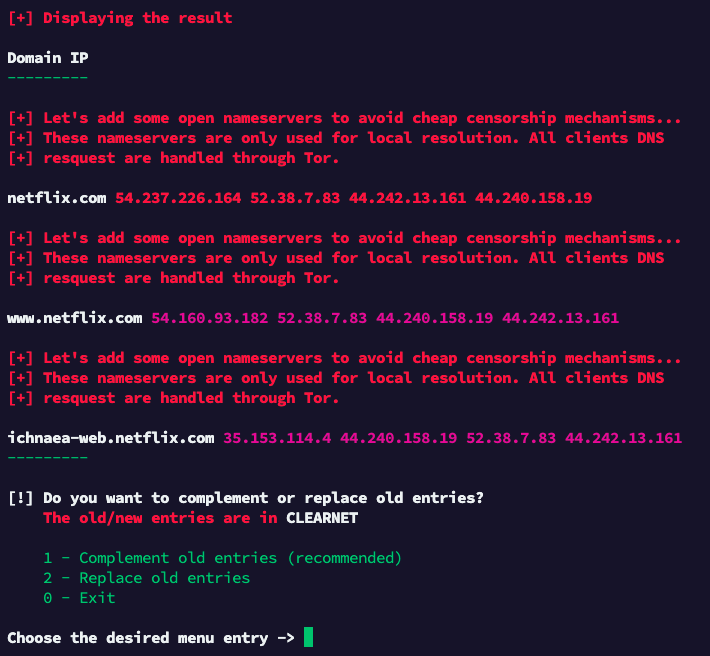
According to the result, the deep scan found an additional IP (54.237.226.164) for netflix.com and two additional sub-domains (www.netflix.com and ichnaea-web.netflix.com), which were used during your interaction. The message about adding open nameservers shows some delay or troubles with resolving the domains. It is safe to ignore this message or, if this is the first deep scan, to repeat it to be sure to cache all subdomains and IP-addresses. In our example, choosing “Complement old entries” makes sense. After choosing that entry, the exclusion list looks like the following: ichnaea-web.netflix.com 35.153.114.4 44.240.158.19 52.38.7.83 44.242.13.161
netflix.com 52.38.7.83 44.242.13.161 44.240.158.19 54.237.226.164
www.netflix.com 54.160.93.182 52.38.7.83 44.240.158.19 44.242.13.161
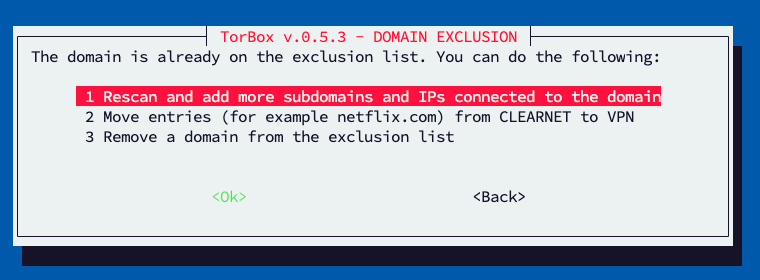
If you use the menu entry again and enter a domain that is already in the exclusion list (for example, netflix.com or www.netflix.com), you will see the following sub-menu:
- Entry 1 will make/repeat a deeper scan of the domain to exclude (more) subdomains and IPs if available and linked with the domain. For more information, see above.
- Entry 2 gives the ability to move the domain from one bucket to the other (CLEARNET to VPN / VPN to CLEARNET).
- Entry 3 will remove the domain from the exclusion list.
Regarding entries 2 and 3, be aware that, for example,netflix.comwill also move/removewww.netflix.comandichnaea-web.netflix.com. However, if you enterwww.netflix.com, thennetflix.comorichnaea-web.netflix.comwill still be in the (old) exclusion list.
- Menu entry 3: Lists the exclusion lists: does what it says.
Menu entry 4: Backup/restore the exclusion lists: displays an explanation how the exclusion lists can be manually saved and restored.
- Menu entry 5: Disable / Enable the AP on wlan1 failsafe: By default, TorBox’s wireless network (the Access Point; AP) is on the interface
wlan0representing the internal wireless chip. However, entry 7 in the main menu changes that because to use the internal chip to connect to the Internet, the AP has to be put onwlan1which is representing the USB wireless network adapter. The big problem is that if TorBox is shut down, the USB wireless network adapter is removed, and TorBox starts again, the user is locked out. To avoid that, TorBox reverts any configuration during the boot, putting the AP onwlan1. Of course, this is not something users want to have when they want the AP stick to the USB wireless network adapter. For them, it is possible to turn off the failsafe feature with this menu entry.
- Menu entry 6: Disable / Enable SSH password login: does what it says. It especially makes sense after generating and using SSH keys for the TorBox SSH login, which can be done in the Configuration sub-menu entry 2.
- Menu entry 7: Forwarding only – tor protection disabled: The “forwarding only” mode for client data traffic will function as a router without tor protection. This feature was a request, but most of the time, it makes only sense in connection with developing and debugging.
Menu entry 7: Activate/deactivate other connection options in TorBox mini’s Main Menu. This menu entry is only displayed on a TorBox mini installation. In a default installation, TorBox mini shows only one connection option, where the Internet is connected through wlan0 , and the client is connected to usb0. However, advanced users may add additional connection options to the Raspberry Pi Zero 2 W and want to change to another connection option, and therefore use this menu entry to activate them again.
• • •
Problems and questions
- TorBox’s wireless manager doesn’t show me any or not all wireless networks (2,5 GHz and/or 5 GHz)! What can I do? –> see here.