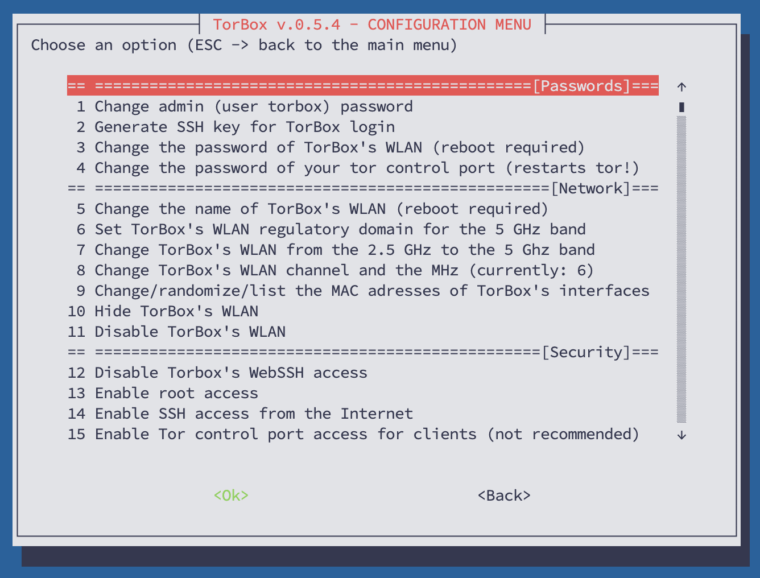
The primary purpose of the configuration sub-menu is to offer a simple way to configure your TorBox. In this sub-menu, you also find all the necessary entries to change the default passwords. You should do that as soon as possible — check the red colored menu entries below. Additionally, this menu gives you the ability to change basic configurations like network, security, tor, and logging settings and install additional software for specific hardware support.
In the following, we look at all menu entries one by one:
- Menu entry 1: Change admin (user torbox) password: That’s the first thing you should do!
- Menu entry 2: Generate SSH key for TorBox login: This menu entry will generate new private and public SSH keys, providing an easy, secure way to log into TorBox. In the end, you will have two files in TorBox’s home directory:
- id_rsa (Private Key): The private key must be downloaded on your client using SFTP (it uses the same login and password as your SSH client). To log into TorBox, you must use an SSH client that supports SSH key handling (for example, Termius) or TorBox’s webssh. The key should be kept secure so that no other users on your computer can read the file.
- id_rsa.pub (Public Key). The public key will stay on the TorBox.
- This menu entry doesn’t disable password identification. However, you will find the according menu entry in the Danger Zone.
- Already existing SSH keys will be overwritten. If disabled, you may temporarily enable password identification to avoid the risk of being
locked out. With replacing the public SSH key, you must replace and test the private key of your SSH client before you log out of the TorBox! - Regardless of the use of SSH keys, the default passwords with entries 1 and 3 should be changed in any case.
- Menu entry 3: Change the password of TorBox’s WLAN: That’s the second thing you should do! A reboot is required to take effect.
Important: Only letters (upper and lower case) and numbers are allowed. The length must be between 8 and 63 characters.
- Menu entry 4: Change the password of your tor control port: The control port is used for controlling tor, usually through other software. To change that password is generally not necessary. If you, nevertheless, change the password, tor restarts automatically.
- Menu entry 5: Change the name of TorBox’s WLAN: Depending on your environment, it could be a good idea to fit in with the name of your wireless network.
- Menu entry 6: Set TorBox’s WLAN regulatory domain for the 5 GHz band: By default, TorBox WLAN regulatory domain is set to the United States, which works in most cases. Depending on the location, however, it may be necessary to adjust the WLAN regulatory domain to use all bands, channels and frequencies and not get in trouble. For more information see here.
- Menu entry 7: Change TorBox’s WLAN from the xx GHz to the xx GHz band: This menu entry changes the TorBox’s WLAN — the one, which the SSH client connects — from 2,5 GHz to 5 GHz or back. If you are in an area with many devices transmitting on 2.5 GHz, a change on the 5 GHz band could solve some problems and provide higher throughput. This is only supported by a Raspberry Pi 3 Model B+ or a Raspberry Pi 4 Model B.
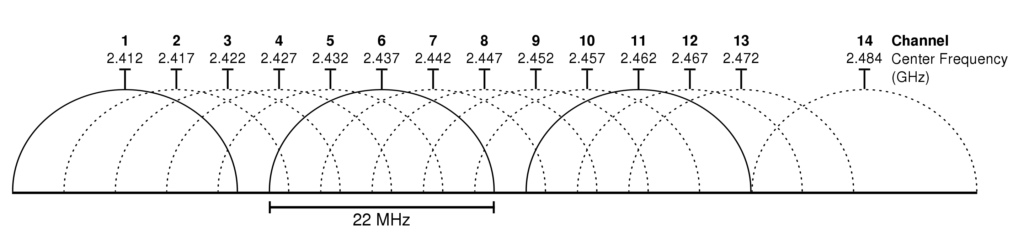
- Menu entry 8: Change TorBox’s WLAN channel and the MHz: This menu entry changes the channel and the frequency of TorBox’s WLAN. If you are in an area with many devices communicating on the same channel you’re using for TorBox’s WLAN, changing channels can solve some problems and increase throughput. It is also true that higher frequencies are associated with higher throughput. However, this also means that more power is required and thus a reliable power supply. Frequencies above 20 MHz are only supported by a Raspberry Pi 3 Model B+, a Raspberry Pi 4 Model B or a Rasberry Pi 5.
Important: 40 MHz is only activated if there is no overlap with other devices. For this purpose, hostapd performs a background scan. This can also be checked with the following command:hostapd -dd /etc/hostapd/hostapd.conf
- Menu entry 9: Change/randomize/list the MAC addresses of TorBox’s interfaces: A MAC address is a unique identifier assigned to a network interface. According to Edward Snowden, the NSA has a system that tracks the movements of mobile devices in a city by monitoring MAC addresses. Therefore vendors started to randomize the MAC addresses on their devices. Since TorBox v.0.5.1, we began to randomize the MAC addresses of the interfaces wlan0, wlan1, eth0 and eth1 by default. However, to overcome captive portals, you can also use the MAC address of another device that has successfully passed through a captive Portal. See here for more information on how to pass through a captive portal.
- Menu entry 10: Hide / Unhide TorBox’s WLAN: If you choose “hide”, TorBox sends empty SSID in beacons and ignores probe request frames that do not specify full SSID. In other words: to connect with your wireless network, the full name of that network must be known. “Unhide” will reverse this behavior.
- Menu entry 11: Disable / Enable TorBox’s WLAN: If at least one client device is connected to the TorBox with a cable, through a VPN connection or an
usb0interface, this menu entry gives the possibility to disable the TorBox WLAN. It can be chosen between a temporary disabling, which lasts only until the next restart of the TorBox, and a permanent disabling. To disable TorBox’s WLAN permanently involves the risk of locking you out.
- Menu entry 12: Disable / Enable TorBox’s WebSSH access: With TorBox v.0.5.1,
websshreplacedshellinabox, which is not maintained anymore. Withwebssh, users don’t need a ssh client because every web browser can jump in. A user on a wifi-client can type 192.168.42.1, someone on a cable-client 192.168.43.1. This functionality comes with a certain risk becausewebsshis not encrypted (this would need a self-signed certificate, which the browser doesn’t support easily). However, this shouldn’t cause any problems because the TorBox AP and its wlan or the connection cable should be controlled by you. By default,websshcannot be accessed from the Internet. If you seek maximum security, you still can keep using an ssh client and even deactivate thewebsshfunctionality with this menu entry.
- Menu entry 13: Disable / Enable root access: In everyday use,
rootaccess is not necessary. TorBox running on Raspberry Pi OS has root access disabled by default. That’s most likely not the case with Debian- and Ubuntu-based installations. In some cases, for example,rootaccess is necessary at the beginning of a TorBox on a Cloud installation until all components are correctly configured and clients can connect using OpenVPN Connect or Tunnelblick to the TorBox on a Cloud. However, even then, from a security standpoint, it is more secure to disablerootaccess after this initial phase. With this menu entry, you can disable or enable root access. Enablingrootaccess will also require a new password.
- Menu entry 14: Enable / Disable SSH access from the Internet: Does what it says – the default is disabled.
- Menu entry 15: Enable / Disable Tor control port access for clients: For security reasons, the Tor control port is only used locally on the TorBox itself and is protected by a password. If someone needs to control tor from a client, he can enable the tor control port access for clients.
Important:
.- To take effect of the change, you must (re-)select the Internet connection in the Main Menu (entry 5-10).
- If the tor control port is enabled for clients, we strongly advised to change the password of your tor control port (entry 3).
- Enabled tor control port access for clients generates warning messages in the Tor log.
- Menu entry 16: Enable / Disable HTTP plain text traffic block: This option blocks all HTTP plain text traffic through Tor by blocking port 80. It should avoid unencrypted data traffic at tor exit nodes, which could break your anonymity (see here). However, it is only a very superficial block, which could help if, for example, a browser requests an unencrypted Webpage (http://). Currently, it does not generally block plain text traffic (for example, Telnet). Also, HTTP plain text traffic from clients using TorBox’s SOCKS 5, in a VPN over Tor or a Tor over Tor situation cannot be blocked Another downside is that not only unencrypted web pages but also other traffic on port 80 are blocked so that probably some applications will not work correctly anymore. However, .onion addresses using “http://” will still work. Instead of using this menu entry, we recommend installing HTTPS Everywhere in the Browser.
- Menu entry 17: Start/Stop excluding slow tor relays: This menu entry will generate a list of tor relays which are slower than the given speed threshold in KB/s. You can set the threshold, but if unsure, we will set it to 4000 KB/s by default, which currently will block less than half of the relays. Excluding slow tor relays may give you a higher and more stable average speed and, therefore, a better user experience. This measure is, therefore, useful if you notice an annoying slow or unstable Internet performance. However, this comes with a price –> a higher risk of deanonymization due to a fewer set of relays. To illustrate possible concerns, take the example of a hypothetical adversary, which adds a lot of excellent performing relays to the tor network to anonymize tor users. In this case, it would be more likely that you are using the adversary’s relays, which could deanonymize users by a correlation attack. For that reason: Do not activate this menu entry if your anonymity has the highest priority.
Important: If activated, please, don’t forget to update the list of excluded slow tor from time to time, using entry 12 in the update and maintenance sub-menu.
- Menu entry 18: Enter the advanced tor configuration editor: This menu entry gives access to the Tor configuration file. You should know what you are doing before you change anything in the configuration file — here, you can break your TorBox. If you are unsure, then contact us. Did you something wrong? You can always overwrite this configuration with the default one, stored in ~/torbox/etc/tor/. After changing the configuration, use the following commands in the editor: CTRL-S to save the changes. CTRL-X to exit the editor.
- Menu entry 19 : Changing the extent of logging: By default, TorBox reduces logging to a minimum. However, the protocol function for Tor remains activated so that the correct operation be determined. Tor ensures that no sensitive information is leaked into the log files. For detailed troubleshooting, the log function can be set to “High”, which effectively means that the normal log function of the operating system is activated.
- Menu entry 20: Erase all log files: It does what it says.
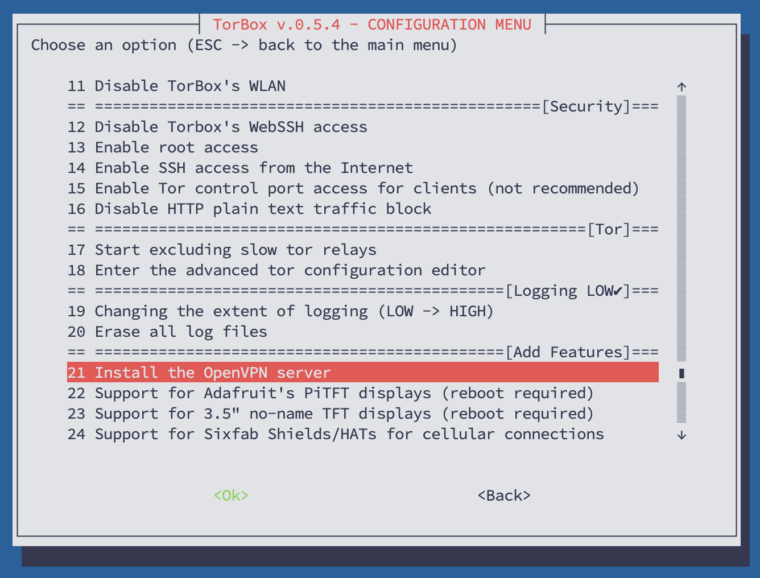
- Menu entry 21: Install the OpenVPN server / Manage the OpenVPN server: Installing an OpenVPN server makes sense in a TorBox on a Cloud installation, or in any case, if TorBox should act as an OpenVPN server. If TorBox does not appear to be installed on a cloud, you need to determine that the installation is on a physical (“real”) box, meaning it is running on actual hardware. The difference is that with the first choice, TorBox assumes that the Internet is connected to a fixed interface, which will be renamed
eth0; with the latter, you can use all interfaces, plus the option to connect the client via OpenVPN.
The installation is straightforward; all default options are pre-selected, and you usually only need to pressEnter. On a cloud installation, the IP address must be accessible from outside the Internet by a fully qualified IP address or through the Internet provider’s NAT (port forwarding). On a real box, use 192.168.42.1 on a WiFi client and 192.168.43.1 on a cable client to be safe. Nevertheless, it shouldn’t make any difference in the end, because the OpenVPN server should listen on all network interfaces.
Regarding the port, we highly recommend using the standard port 1194 for OpenVPN. To handle VPN connections, TorBox must accept traffic on this specific port and cannot route it through the Tor network. It means that using another port number, for example, 443, to avoid a blocking firewall will prevent UDP traffic to port 443 from being routed through the Tor network, which is a substantial security risk. UDP on port 443 is most commonly associated with the QUIC protocol, which was developed by Google and is now used by several major web services and applications to provide faster and more efficient encrypted web connections (for more information, see here). Before using a port other than 1194, you must check if UDP traffic to this port is not being used by another application, which could then compromise your security.
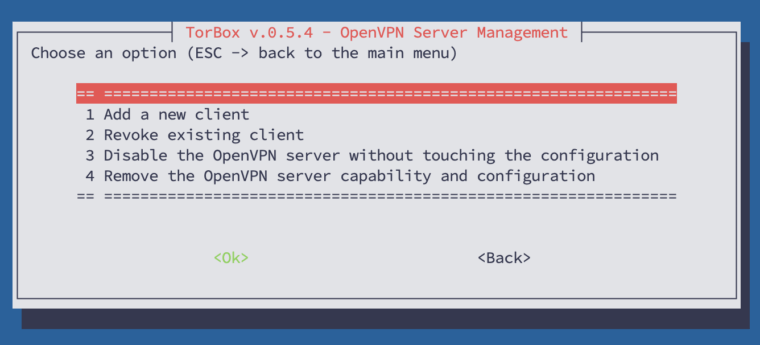
If the OpenVPN server is installed, the menu entry will allow you to manage the OpenVPN server, displaying a sub-menu (see below):
Add a new client: Every client needs itsovpn-file generated on the TorBox. You can add a client with this menu entry, which will generate a newovpn-file stored in/home/torbox. After the generation, you must download theovpn-file to your client machine. You can access it by using a SFTP client (it uses the same login and password as your SSH client). Then use theovpn-file with OpenVPN Connect or Tunnelblick.
The other menu entries do what they say.
- Menu entry 22: Support for Adafruit’s PiTFT displays: A nice way to display TorBox’s real-time statistics (main menu entry 1) is to combine a Raspberry Pi with a PiTFT 3.5″ resistive touch 320×480 from Adafruit (for more information, see here). With this menu entry, the necessary drivers are installed. TorBox has to be connected to the internet and a reboot is required to take effect. Supported are following Adafruit’s PiTFT displays: PiTFT 3.5″ resistive touch 320×480, PiTFT 2.8“ capacitive touch 240×320, PiTFT 2.4″, 2.8″ or 3.2″ resistive 240×320, PiTFT 2.2″ no touch 240×320, Braincraft 1.54″ display 240×240.
- Menu entry 23: Support for 3,5″ no-name TFT displays: Instead of an Adafruit TFT display, it is also possible to use a 3,5″ no-name TFT (for more information, see here). With this menu entry, the necessary drivers are installed. TorBox has to be connected to the internet, and a reboot is required to take effect.
Regarding the use of TFT displays
TorBox’s menus and dialogue boxes have only been adapted for TFTs with a minimal resolution of 320×480. Adafruit’s and 3,5″ no-name TFTs are widely used and are therefore included in the configuration menu. On request, we are happy to support other widespread small screens for the Raspberry Pi.
- Menu entry 24: Support for Sixfab Shields/HATs for cellular connections: This menu entry installs the necessary drivers for Sixfab Cellular Shields/HATs for cellular connections (for more information, see here). Supported are the following Sixfab Shields/HATs: Raspberry Pi GSM/GPRS Shield, Raspberry Pi 3G-4G/LTE Base Shield V2, Raspberry Pi 3G/4G<E Base HAT, Raspberry Pi Cellular IoT Application Shield, Raspberry Pi Cellular IoT HAT, Raspberry Pi Tracker HAT.
• • •
Problems and questions
- Can I hide the name of the wireless network (SSID) of my TorBox? –> see here.
- I’m connected to TorBox, and all is working as expected, but Firefox, Safari and any iOS device don’t display .onion sites. What’s wrong? –> see here.
- Is there a way to force/block TorBox to use an exit node in a specific country? –> see here.
- Should I change the default passwords? How can I change my passwords? –> see here.
- Should I change the name of the wireless network (SSID) of my TorBox? How can I change it? –> see here.
- TorBox’s wireless manager doesn’t show me any or not all wireless networks (2,5 GHz and/or 5 GHz)! What can I do? –> see here.
- Why is Tor so slow – is the Tor network broken? –> see here.