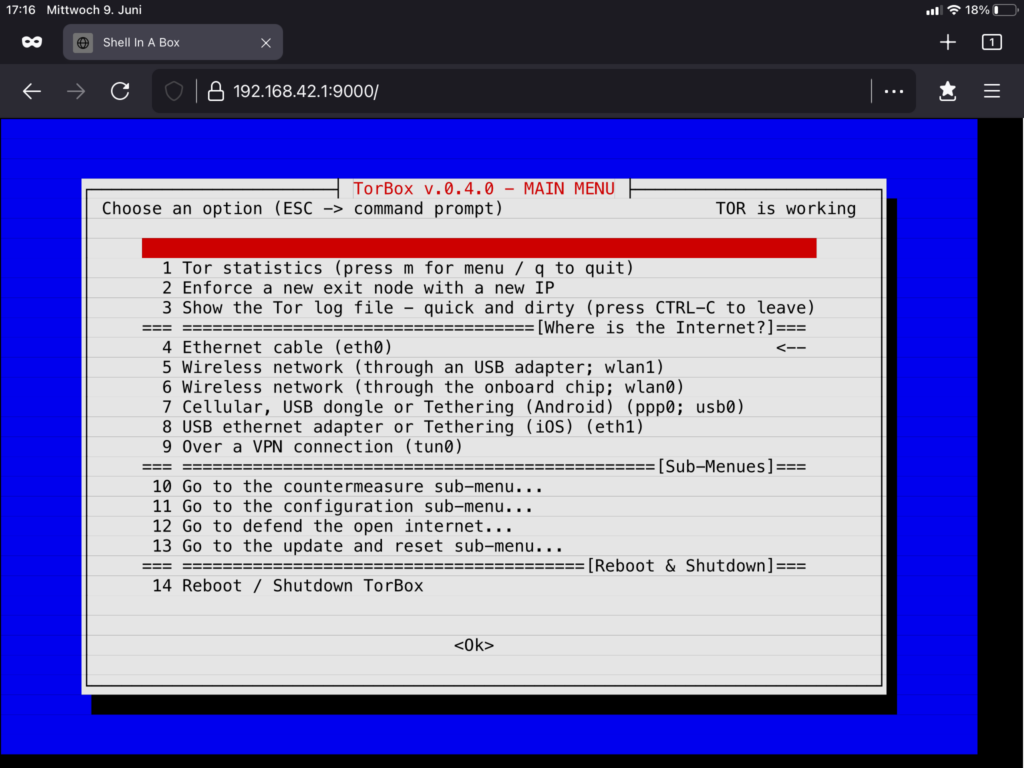
We are very dependent on your feedback! In this release, we have made an effort to implement more of your requests and, again, to improve the usability of TorBox based on your feedback. In this journey to the TorBox v.0.4.1, nyxnor has been a huge support, rewriting the OBFS4 bridge support of TorBox, which is now easier than ever to use. We also implemented experimentally “Shellinabox“, which gives clients to access the TorBox menu through a web browser so that the installation of a SSH client would not anymore be necessary. You can try it out by using https://192.168.42.1:9000 on a WiFi client and https://192.168.43.1:9000 on a cable client. Unfortunately, with the self-signed certificate for its secure connections, browsers will show a warning message during the first connection, which has to be ignored. We are eager to hear your feedback on “Shellinabox”. Do you know better alternatives? Let us know!
With the TorBox GitHub repository, it is straightforward for everyone to report issues or to change the code and to propose it in a pull request. Because we continue to travel around, it sometimes needs a little more time to address the issues and proposals. This is especially true for the TorBox website:
Over the following weeks, we will update the TorBox website to reflect all the changes introduced with TorBox v.0.4.1. Until then, some information could be outdated and refer to the older version.
TorBox Image (about 940 MB): v.0.4.1 (13.06.2021) – SHA-256 values
TorBox Menu only: v.0.4.1 (13.06.2021) – SHA-256 values
Since we had to install additional software packages and update the configuration files, we recommend using the new image rather than updating an existing system. However, we have added a short guide at the end of this post for those who absolutely must update from the previous version (not older!).
Changelog: v.0.4.0 (10.04.2021) –> v.0.4.1 (13.06.2021)
- Update: The system is based on Raspberry Pi OS “Buster” Lite with a Linux Kernel 5.10.17 and Tor version
- 0.4.5.8.
- Update: Internal list of bridges updated.
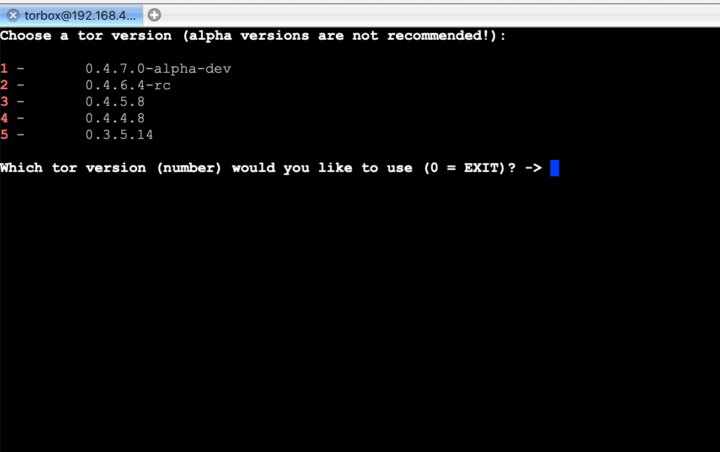
- New: Installed with one of the installation scripts and using the option “–select-tor” makes it possible to chose the to be installed tor version.
- New: The installed tor version can be updated or changed with entry 4 in the Update and Reset sub-menu, where “DEFAULT” installs the latest stable version and “EXPERT” gives access to a variety of TorBox versions, including the -rc and -alpha versions.
- New: A new script was added to the torbox folder but not yet included in the TorBox menu, which should automatically react to log-related events. The idea behind it is that, with the next version, TorBox can automatically handle a disconnection from a WiFi network or the tor network. For example, if the tor log file indicates that the entry guard is failing, TorBox should choose a new entry guard in the background. If successfully tested, the necessary rules will follow later and are expected to be integrated into the Countermeasure sub-menu.
- Fixed: Using entry 10 in the Configuration sub-menu to enable the SSH access to TorBox from the Internet was not permanent when chosen so, but was permanent when chosen temporary (mentioned by bhafer, see details in issue #46).
- Fixed: SOCKS v5 port for destination address stream isolation was falsely set on port 9051 used for the Tor Control Port. The port is now changed to 9052.
- Fixed: The Tor Control Port (9051) is now accessible from clients (mentioned by bhafer, see details in issue #46).
- Fixed: OBFS4 bridges with IPv6 addresses are now handled correctly (see details in issue #55).
- Fixed: After the installation, the go source package wasn’t removed from the home directory.
- Fixed: All known problems and bugs listed in the Blog entry to TorBox v.0.4.0.
- Improved: The use and handling of OBFS4 bridges are now more intuitive and in line with the use of the Meek-Azure and Snowflake bridges. There is no need anymore to activate OBFS4 bridge functionality in two steps. Also, the explanation about the functionality of bridges, pluggable transports and their use was completely rewritten. This amazing work was done by nyxnor – thank you very much!
- Improved: If one of the pluggable transports (OBFS4, MEEK, SNOWFLAKE) will be activated, another already running pluggable transport will be automatically deactivated.
- Improved: When installed from the image file, with the first start of the TorBox menu, the SSH server keys will be replaced by new ones. (mentioned by rsaxvc, see details in issue #40).
- Improved: All installation script can be run several times, for example, if the first installation attempt was not successful or when the system has to be reinstalled.
- Improved: The support for Ubuntu 20.04 / 21.04 and Debian 10/11 systems.
- Improved: Clean up the code of the TorBox Wireless Manager.
- Improved: We removed the first blank line to use the maximum available space for the entries in all menus. Also, the sub-menu to set up an OBFS4 relay server on the TorBox looks now more similar than the Countermeasure sub-menu.
- Improved: Restarting tor is now accessible from the Main menu.
- Improved: The slack space of the TorBox image is now overwritten by zeros (with the program zerorfree). This probably is why the compressed image of TorBox v.0.4.1 is almost 220 MB smaller than the image of TorBox v.0.4.0 (thanks goes to rsaxvc for the suggestion, see details in issue #39).
- Experimental: “Shellinabox” added to the TorBox and setup on port 9000. With “Shellinabox”, users can access the TorBox main menu through a web browser using https://192.168.42.1:9000 on a WiFi client and https://192.168.43.1:9000 on a cable client. Unfortunately, with the self-signed certificate for its secure connections, browsers will show a warning message during the first connection, which has to be ignored. To use a secure connection between the web browser and Shellinabox, the user must accept this certificate. We are eager to hear your feedback on “Shellinabox”. Do you know better alternatives? Let us know!
How to update from TorBox v.0.4.0 (10.04.2021)?
To update a TorBox v.0.4.0 (10.04.2021) installation, you can perform the following tasks. This deletes all your custom made configuration but not alter your bridge relay keys. Nevertheless, we recommend, if possible, using the new image.
- Please, make sure that TorBox has Internet connectivity.
- Update the system: Go to the Update and Reset sub-menu, update the base system, the TorBox menu (entry 1 and 5) and after that, update to the newest version of tor (entry 4).
- To ensure that all necessary packages are installed, execute the following commands (please, make sure that you copy the entire line!):
sudo apt-get -y install hostapd isc-dhcp-server obfs4proxy usbmuxd dnsmasq dnsutils tcpdump iftop vnstat links2 debian-goodies apt-transport-https dirmngr python3-pip python3-pil imagemagick tesseract-ocr ntpdate screen nyx git openvpn ppp tor-geoipdb build-essential shellinabox
- Replace the changed configuration files:
# Backup in case
sudo cp /etc/tor/torrc /etc/tor/torrc.bak
# ATTENTION: This will overwrite your modifications as well as the configuration for the OBFS4 bridge relay
# If you run a bridge relay use "backup/restore the Bridge Relay configuration"
sudo cp etc/tor/torrc /etc/tor/
sudo cp etc/motd /etc/
sudo cp etc/hostapd/hostapd.conf /etc/hostapd/
sudo cp etc/default/shellinabox /etc/default/shellinabox
sudo mv /etc/shellinabox/options-enabled/00+Black\ on\ White.css /etc/shellinabox/options-enabled/00_Black\ on\ White.css
sudo mv /etc/shellinabox/options-enabled/00_White\ On\ Black.css /etc/shellinabox/options-enabled/00+White\ On\ Black.css
sudo systemctl restart shellinabox.service
sudo cp torbox/etc/hostname /etc/
sudo cp torbox/etc/hosts /etc/
The commands above should work. Alternatively, you could also go to the Update and Reset sub-menu and reset the entire TorBox configuration from there (entry 8).
- Reboot TorBox.
Known problems and bugs
- BUG: Using the installation scripts with the option
–select-torboxor using the EXPERT option in changing/updating tor with the Update and Reset sub-menu doesn’t show all relevant recent tor versions. You can fix these bug by updating the TorBox menu (update and reset sub-menu entry 5). BUG FIXED✔︎
.
- LOOK&FEEL: Tor displays the following warning: “You have a ControlPort set to accept connections from a non-local address. This means that programs not running on your computer can reconfigure your Tor. That’s pretty bad, since the controller protocol isn’t encrypted! Maybe you should just listen on 127.0.0.1 and use a tool like stunnel or ssh to encrypt remote connections to your control port.” This warning is generated because the Tor Control Port (9051) is now accessible from clients (see details in issue #46). However, if you control the clients and/or if you change the password of the Tor Control Port (entry 3 in the Configuration sub-menu), it doesn’t constitute a security risk. If this is not acceptable, the following entries can be removed from /etc/tor/torrc:
ControlPort 192.168.42.1:9051
ControlPort 192.168.43.1:9051
Don’t removeControlPort 9051!! Our plan for TorBox v.0.4.2 is to disable the accessibility of the Tor Control Port from clients again as default but to integrate into the Configuration sub-menu an option to enable/disable the accessibility.
Your feedback is welcome!!
We hope this version pleases you. However, we are dependent on feedback. It is not just about fixing bugs and improving usability, but also about supporting additional interfaces and hardware in future releases:
- What do you like?
- What should be improved (why and how)?
- What would you like to see next? Which features do you request?

Please allow a setting to run Torbox PI’s as standard Tor Relays, in addition to OBFS4 bridges. I want to use Torbox to Run standard tor bridges.
What benefit is this supposed to bring to the general public?
This look like a prepackaged fbi spying os
This is why we provide a detailed manual how to build a TorBox by your own. Luckily, you don’t have to download our image or installer scripts.
Hello, if I activate the option to operate my own OBFS4 bridge and connect my computer to it via wifi, will my own traffic be routed via the OBFS4 bridge? or do I have to set up a separate TorBox and then connect it to my OBFS4 bridge?
So far, the idea is that you either activate an OBFS4 Bridge Relay in an uncensored environment, or you activate the OBFS4 bridge support for your clients.
I guess it doesn’t make sense to run an OBFS4 Bridge Relay in a censored environment. However, someone may want to use the OBFS4 bridge support and the OBFS4 Bridge Relay together in an uncensored environment. If this is your intention, it would be the best to open an issue on TorBox’s Github page. I can change the code accordingly, but I would need your feedback on how it works in real-world conditions.
If you solely want that all traffic from your connected devices goes through tor using OBFS4 bridges, you only have to activate the configured OBFS4 bridges under the Countermeasure sub-menu.
I want the traffic of my devices to run over my own OBFS4 bridge. The devices are connected to the PI on which the OBSF4 bridge runs. If my TorBox runs as an OBSF4 Bridge and I use devices on it, won’t my own traffic automatically be routed through my own OBSF4?
If not, I’d like to open an issue on github.
I do this because I am in an uncensored environment and want to make my bridge available to the network. At the same time I want to achieve that my ISP does not see that I am communicating through TOR. OBSF4 Bridges do that too, right?
Please open an issue on TorBox’s Github. It is easier to discuss the issue and possible solutions on Github than here. I already created a new branch, called “OBFS4-bridge-and-relay”, which has the changes to allow using OBFS4 bridge relay and OBFS4/MEEK/SNOWFLAKE bridges together. It would be helpful if you could test the new branch (I will help you with that if needed) and give me feedback. After some additional tests, and if your feedback is positive, I will merge the changes into the master branch.
Hi so I wrote something to you on github. https://github.com/radio24/TorBox/commit/d5b0045eec2e79c60dfd33b0239a5d1e4291597f
Hope the comment is placed correctly xD I’m github noob and unfortunately I can’t code anything. So sorry if I do something wrong. How
Thanks to the developers for the product.
I have a question: After installing Torbox on the Raspberry, the internet comes in through the lte modem (eth1, option 9 in the main menu).
Through wifi everything works fine, but when I connect a PC (Win or Linux) via ethernet port, there is no internet on it. What am I doing wrong? I would like to get the Internet on the wire as well.
If I understand you right, you want to have an ETH1 (Internet) –> WLAN0 / ETH0 configuration, right?
Important is that first, you connect all clients, and then you chose entry 9 in the main menu).
If this doesn’t help, did you ever try to do it the other way around: ETH0 (Internet) –> WLAN0 / ETH1 ?
If this also doesn’t help, then it is best you add an issue on our Github page and provide us with more details and the files listed in the FAQ.
What is your advice on using Tails in a Torbox network? Do you see any issues with doing that (anything that would reduce privacy), or is the only “issue” that it’s slower than it needs to be?
The case using Tails with TorBox together was already discussed in issue #68 and in the FAQ.