Update – 10.03.2023
With this update, we brought TorBox’s software to the latest state: Raspberry Pi OS “Bullseye” lite 64bit (Release date: February 21st, 2023) with the Linux Kernel 5.15.84 and Tor version 0.4.7.13 with obfs4proxy version 0.0.14 and Snowflake 2.5.1. We also fixed some critical bugs in connection with Snowflake and Meek, which blocked the correct functioning of these two bridges (see below). We added a better time synchronization to avoid problems with building tor circuits, especially in cases without Internet connectivity. As always, we appreciate feedback, ideas, bug reports, pull requests etc.
TorBox Image (about 1.1 GB): v.0.5.2 (10.03.2023) – SHA-256 values
TorBox Menu only: v.0.5.2 (10.03.2023) – SHA-256 values
Update – 16.02.2023
If TorBox is started for the first time, and the connection is selected through WiFi by the “first run” script, then synchronising the system clock certainly fails. As a consequence, tor will not be able to build a circuit. With this update, the “first run” script will newly display the system time and allow the user to synchronise the system clock automatically or manually. Also, we integrated a new menu entry in the Update and Maintenance submenu to synchronise the system clock.
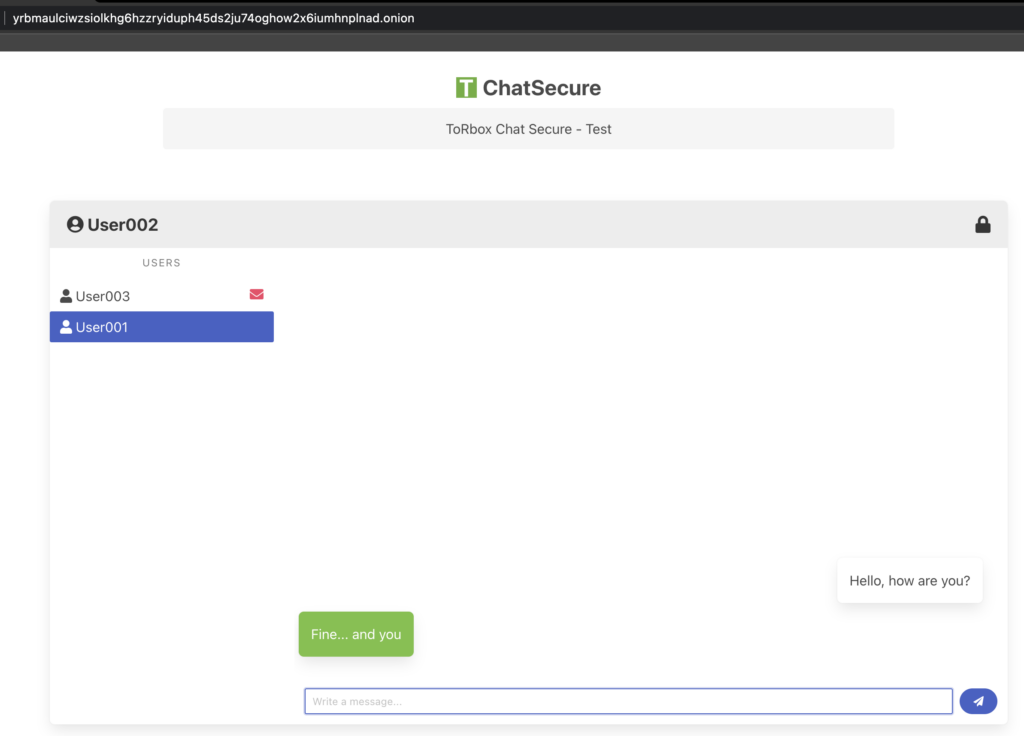
More than a year ago, we started to integrate Onion Services into TorBox. In the sub-menu Onion Services, it is easy to set up an Onion Service and to share a folder or a simple website, as well as TorBox File Sharing (TFS). With TorBox v.0.5.2, we additionally integrated TorBox Chat Secure (TCS). This is a secure way to communicate between two people using a specific onion domain. We still have some ideas for Onion Services for the following TorBox versions, for example, to allow users to install MariaDB/MySQL, PHP and WordPress through the menu so that dynamic website can be easily hosted on TorBox as an Onion service. Another idea currently under review is the further development of TCS into a chat room where several people can chat. With all these or other ideas, as well as eliminating errors and simplifying processes, active feedback from users is essential. Also, some bugs have been fixed in the new version, mainly as they occurred in our daily use. However, we still hear far too little from users.
Since we had to make substantial changes in the configuration files, it is recommended to use the new image or reinstall TorBox using one of our installation scripts.
Changelog: v.0.5.1 –> v.0.5.2 (02.01.2023)
- Update: The system is based on Raspberry Pi OS “Bullseye” lite (64-bit) with Linux Kernel 5.15.76 and Tor version 0.4.7.12 with obfs4proxy version 0.0.14 and Snowflake 2.4.1. Obfs4proxy version 0.0.14 will fix some critical obfuscation bugs. All installation scripts are updated to work with Raspberry Pi OS “Bullseye”, Debian 11 and Ubuntu Server 22.04 LTS. Additionally, we also updated TorBox’s internal list of OBFS4, Snowflake and Meek-Azure bridges.
- Update: Support for additional network drivers. We also moved the installation of additional network drivers from the installation to the “first use” script. Thus a kernel update during the installation will not break the installation of the drivers.
- Update: Noname 3.5″ TFT display support.
- New: TorBox Chat Secure (TCS) in the Onion Service sub-menu. TCS is a straightforward way to communicate between two people with safeguarding anonymity. No information about the conversation is stored on the TorBox.
- New: Support of handling multiple Snowflake bridge lines in the torrc. Similar to OBFS4 bridges, this feature will make circumventing tor blocking in countries like China, Iran, Russia and Turkmenistan more effective because you can select the right Snowflake bridge to activate according to the country in which you are located. Snowflake bridge lines can be activated, added, removed, deactivated and listed. However, currently, Snowflake supports only one active bridge line. If you activate several bridge lines, only the first will be used.
- New: Related to the point above, TorBox’s automatic fetching feature for OBFS4 and Snowflake bridges support now country-specific bridges. However, country-specific bridges are currently available only for certain countries (see also here). Also, if available, TorBox will fetch up to three bridges at once. To make these new features possible and to help people in censored countries, TorBox fetches bridges using the moat distributor. The moat distributor is an API that clients use to get bridges and circumvention settings. Clients must use domain fronting to avoid censorship when connecting to the API. In the case of TorBox, users in censoring countries have to use Snowflake or Meek-Azure to get more OBFS4 bridges (see here for more information).
- New: The “first-use” script is now supporting Snowflake, with the idea to make it easier for people in strictly censored countries to get TorBox running.
- New: Exclusion of slow relays (entry 15 in the Configuration sub-menu). Thanks to Nonie689 for bringing this idea up! Please test it extensively and give us feedback because we are considering adding this feature to the “first-use” script.
- New: Backup and restore cover the entire TorBox configuration (OBSF4 Bridge Relay, Onion Services and shared folders included). It can be found centrally in the Update and Maintenance sub-menu.
- New: Onion Services support client authorisation, which makes an Onion Service private and authenticated. With the former version, TorBox could control clients’ access from outside to TorBox’s Onion Services. With this version, we can provide the internal clients behind TorBox access to other Onion Services using the client authorisation on TorBox. In other words, if you register the server’s private key under the Onion Service menu entry 13, then not only the TorBox itself will have access to the Onion Service but also all client devices for which data traffic is routed through the TorBox, even if TorBox itself provides the Onion Service (in this case, TorBox is server and client). However, after the initial start, it can take up to 30′ minutes to take effect (thanks for figuring this out goes to nyxnor).
- Fixed: If Onion Services with shared folders were deleted, the removal of Nginx’s configuration failed.
- Fixed: Automatically adding bridges will work again. The script
bridges_get.pystarted to fail because the HTML generated byhttps://bridges.torproject.org/bridges?transport=obfs4%27has changed –> we added a patch written by lockcda (thanks for that!). Also, there is a bug in installing mechanise 0.4.8. For that reason, we still work with version 0.4.7. Anyhow, by using the moat distributor, this kind of problem should be gone. - Fixed: GitHub changed how it replies to the script’s question about the available tor versions. The changed behaviour broke the installation and update scripts, which are fixed now. We also removed the tor-specific entries in
torbox.runbecause of the complexity, and it doesn’t give an added value. - Fixed: Blocking HTTP plain text traffic doesn’t block access to webssh and .onion addresses anymore, which both work through HTTP. Please test it extensively and give us feedback because we are considering activating this feature as default in the next TorBox version.
- Fixed: Under certain circumstances, TACA, even if activated, couldn’t synchronize the clock.
- Fixed: Sometimes, pressing the ESC key didn’t close the menu, instead, it reloaded again.
- Fixed: The WPA password has to be between 8-63 characters – if the user changes this password, TorBox has to check it. Thanks to DEC-entralized finding that bug.
- Improved: To activate, remove and/or deactivate OBFS4 and Snowflake bridges, you no longer have to enter numbers of the concerning bridges, which you had to look up in the list. With this version, you can easily select the bridges you want to manipulate.
- Improved: OBFS4 and Snowflake bridges can be added and removed regardless of the actual type of connection. It gives the user, for example, the possibility to connect the tor network using Snowflake to automatically fetch country-specific OBFS4 bridges and then switch to OBFS4, which is more performant and more reliable than Snowflake.
- Improved: A new method of installing obfs4proxy ensures that the latest version is used. If the URL to the obfs4proxy repository is blocked, the version from the distribution will be installed, which could be outdated. Updating the base system in the Update and Maintenance submenu obfs4proxy will also be updated.
- Improved: The configuration reset using menu entry 6 in the Update and Maintenance submenu.
- Improved: The support for Ubuntu as the underlying operating system.
- Improved: Leaving the tor log with q instead of CTRL-C (improvement for the usability of webssh)
- Improved: If configured, the OBFS4 Bridge Relay will start directly after the boot. There is no need to log into the TorBox menu.
- Improved: The handling of the countermeasure against tightly configured firewalls in the “first-use” script. The underlying problem is that bridges usually don’t work correctly with the countermeasure against tightly configured firewalls being activated. However, depending on the situation, sometimes it works.
- Improved: Faster boot time due to changes in
rc.local. Also,wlan1andppp0connections to the internet should be automatically reestablished during start-up if used before the restart. Thanks to ipwebnl, who mentioned the need to improve this. - Removed: Additional USB wifi drivers from Fars Robotics due to missing updates for one year now. We already replaced these drivers with others from dedicated GitHub sites but kept the possibility to switch back if necessary. The fact is that intensive tests show that the replacements are working even better.
- Removed: Vanguards because there is nothing new happening on that project. It may be because parts of Vanguards were implemented in newer tor versions. The problem is that I’m not sure if this creates interferences. Last but not least, I didn’t see any positive effect since its implementation.
- Removed: In the Update and Maintenance sub-menu: Force to deactivate the OBFS4 mode.
- Removed:
http://www.torbox.chas a jump-site to trigger for a captive portal becausetorbox.chwill no longer support insecurehttpaccess for security reasons. - Removed: The restriction that local DNS resolution will be solely resolved through tor because this was the cause of many problems. TorBox needs direct DNS resolution with Bridges, captive portals, VPN connections, time synchronisation, and other maintenance tasks. These functions must work regardless of whether or not tor has a connection with the tor network. That said, data traffic from the connected clients, which has to be protected, is completely routed through tor (including DNS requests). TorBox is configured so that any direct DNS requests from clients are blocked. See also here.
• • •
How to update from TorBox v.0.5.1?
Again: Since we had to make substantial changes in the configuration files, it is recommended to use the new image or reinstall TorBox using one of our installation scripts. Nevertheless, you can perform the following tasks to update a TorBox v.0.5.1 installation. It will delete all your custom-made configurations.
- Please, make sure that TorBox has Internet connectivity.
- Go to the Update and Reset sub-menu, update the TorBox menu and reset TorBox’s configuration files (entries 1 and 6).
- Manually compare if
torrcin/etc/tor/torrc(compare with the GitHub version) and the runfile (run/torbox.run-> compare with the GitHub version) have similar entries. If unsure, just copy the versions from the GitHub repository over the ones on your system (/etc/tor/torrcand/home/torbox/torbox/run/torbox.run). - Reboot TorBox, and again, make sure that TorBox has Internet connectivity.
- Go to the Update and Reset sub-menu, and update the base system (entries 1).
- Reboot TorBox, and again, make sure that TorBox has Internet connectivity.
- Update the rest in the Update and Reset sub-menu: additional network drivers with entry 2, and tor with entry 4
- Reboot TorBox.
We need your feedback!!
We hope this version pleases you. However, we are dependent on feedback. It is not just about fixing bugs and improving usability, but also about supporting additional interfaces and hardware in future releases:
- What do you like?
- What should be improved (why and how)?
- What would you like to see next? Which features do you request?
With the TorBox GitHub repository, it is straightforward for everyone to report issues or change the code and propose it in a pull request. Because we continue to travel around, it sometimes needs more time to address the issues and proposals.
For future versions, it is essential that we know what you need and want to see from the Onion Services implementation. Please feel free to use the discussion forum to tell us your needs.
• • •
Known problems and bugs
BUG: Snowflake and Meek don’t work. Snowflake is showing the following error: Managed proxy "/usr/bin/snowflake-client": broker failure dial tcp: lookup cdn.sstatic.net on [scrubbed]: read udp [scrubbed]->[scrubbed]: i/o timeout.
The reason is that because of a bug, we block local DNS resolution for Snowflake and Meek. You can fix the bug by updating the TorBox menu (update and maintenance sub-menu entry 5) and reselect the source of the Internet (main menu entries 5-10). BUG FIXED✔︎
PROBLEM: The Countermeasures sub-menu entry 17 should connect the TorBox to a VPN server without routing the tor data traffic through the VPN. It doesn’t seem to work with an Internet connection from a wireless interface (wlan0 or wlan1). It should be that when we tested this feature, we only used cable as an Internet source (eth0). Unfortunately, currently, we cannot test this hypothesis. It may also have something to do with the configuration in the .opvn file. Therefore we would be glad to hear feedback from people who successfully or unsuccessfully tried this entry. RESEARCH ?