Finally! I’m happy to announce the release of TorBox v.0.23. During the last half-year, I tested the functionality under real-life conditions, and I’m pleased with the overall stability of the system (if the power supply is reliable enough). Currently, I receive only a few feedback from the community. Therefore, one of my goals for 2019 is to find more contributors who are motivated to give feedback and to help to improve the functionality and security of the system, but more about that later…
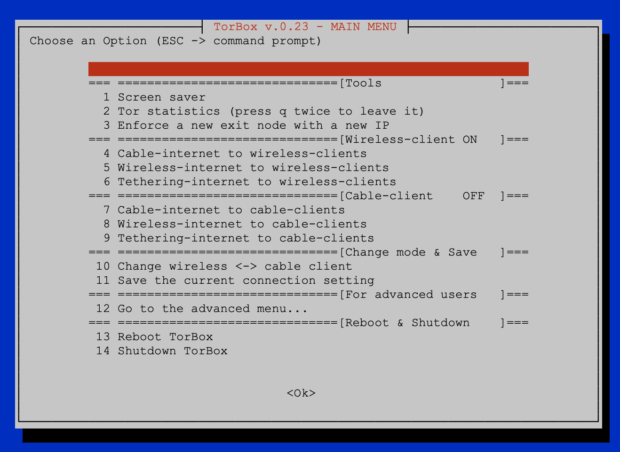
Changelog pre-v.0.2.3 (02.12.2018) —> v.0.2.3 (09.01.2019)
- New: The first noticeable improvement is the size of the image file: it is only a little bit more than 900 Mbyte (compared to 1.4 Gbyte of the last version). This reduction of size was made possible by shrinking the image. At the first start, the image automatically expands over the entire free partition. After an automatic reboot, the system is available for use – user interaction, screen, and peripherals are not required. After 2-3 minutes, when the green LED stops to flicker, connect your client to the new WiFi “TorBox023”. Then use an SSH-client to access 192.168.42.1 (username: pi / password: CHANGE-IT). Now, you should see the TorBox menu. Choose the preferred connection setup and change the default passwords as soon as possible (the associated entries are placed in the advanced menu). TorBox needs at least a 4 Gbyte SD Card, but 8 Gbyte is recommended.
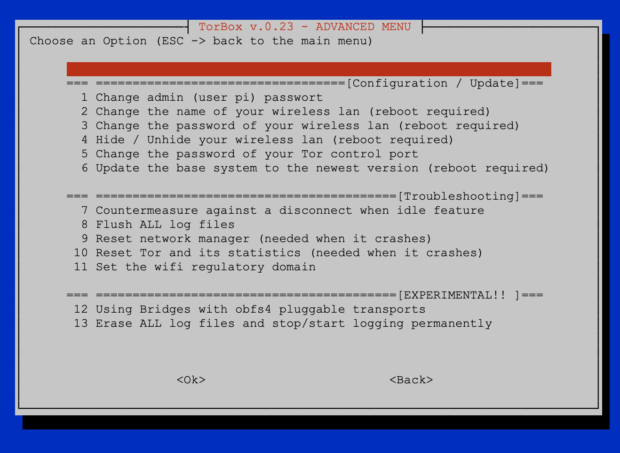
- New: The ability to configure TorBox with bridges that use obfs4 pluggable transport capability to overcome censorship. It is still in experimental status, but with detailed feedback, I will be able to improve and extend this feature for the next version. It works like that: after selecting the connection in the main menu and if Tor Statistics doesn’t show any link to the Tor Network, then additionally the user can try the bridge function in the Advanced Menu. To be honest: the whole thing took a lot of nerves out of me, not so much because of the configuration, but because there seem to be quite a few bridges that don’t work (or don’t work with my network environment). So my advice is, if necessary, to enter 3-6 bridges and to wait at least 5 minutes even though error messages can be seen (someone in a country with state censorship told me that he needs up to 15 bridges). Probably, I will change the implementation of that feature in the future; actually, the improvement of this very important feature will be the main focus for the development of the next pre-v.0.24. That’s why I need your feedback and ideas on these. However, one thing in advance: currently, I don’t see any way to get the bridges automatically (at least as long as we deal with shell scripts :-/).
- New: I noticed that some free Internet provider at airports, hotels, coffees, etc. just cut the connection after a particular time without network load. A “normal” device would probably reconnect, but this doesn’t work with TorBox. That’s why there is now an entry in the Advanced Menu that provides a constant ping for a minimal data stream. At least with Starbucks, this worked :-).
- New: The localization is now in English by default, the time should remain set to UTC, and ntpdate fetches the correct time at startup … from this point of view there is no urgent need for an additional configuration. However, I added to the Advanced Menu the possibility to set a “Wifi Regulatory Domain”. The current setting is “unset” or “world”, which is quite broad, but if someone has problems with it, he can change it now. Currently, the two-letter country code has to be chosen from https://wikipedia.org/wiki/ISO_3166-1_alpha-2. At this point, I need your feedback, if you need that feature at all and if I should improve its usability.
- New: I also added a runtime file where TorBox stores certain global variables. There isn’t much in it yet, but it might become a kind of configuration file in the future.
- Updated: The system is based on Raspbian “Stretch” lite with Linux Kernel 4.14.79 and Tor version 0.3.4.9.
- Updated: For security reasons, the Bluetooth capabilities are disabled on the provided image.
- Updated: The feature to overcome captive portals has been so stable since last summer that I was able to remove all alternative strategies and test scripts. Now, the captive portal solution works for all connection types – and if someone is mistaken, it doesn’t matter — he can click through the procedure. For security reasons, the user has, however, the possibility to abort before establishing an insecure connection.
- Updated: Experimentally, I had already integrated the possibility of cable-TorBox-cable connections before, but I wasn’t that happy about it. I have entirely reworked this first approach. Now the user can choose between WiFi- or cable-client in the main menu. The user can also switch back and forth, but he has to make sure that he can log in with the chosen client.
- Updated: The update function is now more reliable (now with the latest stable Tor release).
- Updated: All menus and display screens should be viewable on a 3.5“ screen, on a mobile phone or tablet. Besides, the menus are better structured, and I have tried to make the information screens more understandable. Let me know, your thoughts about it.
- Updated: As for DNS leaks, I’m a bit paranoid, so dnsmasq is turned off on TorBox by default, and any DNS queries made locally on the device (that is, by the user logged in via ssh in the shell) are recorded in the log file.
- Minor fix: The menu entry to flush all log files, flushes now “~/.bash_history” too.
- Minor fix: Some minor bugs in the configuration part in the advanced menu.
- Removed: The ability to reset the entire network settings (was located in the Advanced Menu). This feature isn’t necessary anymore, and it wasn’t very useful.
- Tested: With Raspberry Pi 3 Model B and Raspberry Pi 3 Model B+ (max achieved throughput: 2.3 Mb/s). I continue to test the integration of the PiJuice, a portable power platform for the Raspberry Pi, but it seems that the permanent power supply is not reliable enough to enable stable WiFi-TorBox-WiFi connectivity. For portable use, my best experience is made with the RS Pro PB-10400 Power Bank, 5V / 10,4Ah.

Last but not least, I’m coming back to my desire to expand the number of contributors. I have about 4 Raspberry Pi 3 Model B to give away for free (SD Card with pre-installed TorBox v.0.23 included). If you want one of these Raspberry Pis than send me an email explaining why I should send you one and what you are willing to contribute to the project.
